Azure security

What is “the cloud” anyway? There are several descriptions and explanations and one of them is: “Cloud computing is an information technology model that enables global access to shared pools of configurable system resources that can be provisioned quickly, with minimal management effort, usually over the Internet.”
The other definition could be that “the cloud” is “the practice of storing regularly used computer data on multiple servers that can be accessed through the Internet.”
Either way, “the cloud” is by many viewed as a powerful way of transforming their businesses. By using any of the Cloud Computing Models, we can achieve more in less time, usually with significant cost savings.
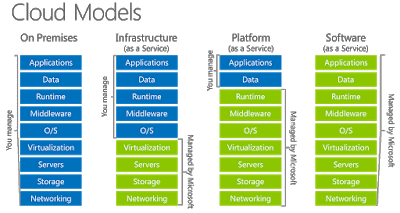
Whether you use Infrastructure as a Service (IaaS), Platform as a Service (PaaS) or Software as a Service (SaaS) Cloud Models you still must think about security within your area of responsibility. Depending on the Cloud Model, each party ensures the security of the layers within their own management area.
Some of the Microsoft’s areas of responsibility is physical security of the datacenter, adequate personnel employment, legal compliance, datacenter hardware and software security and several others.
In a IaaS model for example, Azure Virtual Machines (VM) bring you the freedom of choice between multiple VM sizes, speed of deployment, without the need for expensive hardware. Then, not having the hardware your VMs are running on does not mean you don’t have responsibilities. The usual applies: VMs’ Operating System security has to be well-maintained, ensuring the OS is updated, with antimalware solution deployed including most recent detection database. Additionally, you are responsible for the Virtual Network (VNet) security, storage and application security as well. You might think: “That’s easy, I can do that!” Sure, you, as an experienced systems administrator or systems engineer, are perfectly capable of doing that but as the numbers of VMs, VNets, databases, storage, applications get bigger, protecting valuable assets gets harder and harder. Keeping up with updates, rules and monitoring the infrastructure is no easy task and with many security tasks, recommendations and alerts something might slip out of your attention.
That’s why Microsoft created Azure Security Center, a central security place, dashboard, console. In one word (well, in few words, actually) – “The Place to go for Security in Azure.” As Azure is expanding, adding more functionality, features and services, Azure Security Center (ASC) is evolving and expanding too. It is still far from being “the only” place to go for strengthening security in Azure but certainly, it is the first one to visit.
Let me briefly explore the main Azure Security Center (ASC) capabilities and how ASC helps you increasing security in Azure.
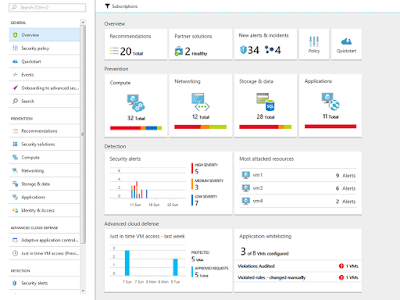
The first thing you notice when opening ASC is the simplicity, clear overview and colour coding. Even if you have not seen ASC dashboard before, it is immediately clear that “red” colour screams for “Alert” or “Attention” while “green” represents something “Looking good” or “Okay”. It is designed around Prevent-Detect-Respond philosophy with additional Advanced Cloud Defense capabilities.
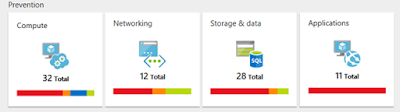
The Prevention part gives you an instant overview of the security state of four principal areas or Azure resource types ASC covers: Compute, Networking, Storage & Data and Applications. I’ll mention just some of the recommendations and monitoring capabilities ASC offers.
Compute section gives you recommendations to VMs, their operating system state, OS security configurations, Azure Storage Account encryption, state of antimalware solution.
Networking alerts you if a firewall or Network Security Groups (NSG) need to be set up or if there is a NSG rule that needs your attention.
Storage & Data enables you to monitor the state of auditing and threat detection on SQL servers and databases.
Application security helps you to enhance the protection of Azure resources by adding a web application firewall and finalise its configuration.
Identity & Access does not have its graphical representation on the main dashboard, but you access it by clicking on the left menu.
Monitoring identity activities pays off because you can take preventive measures or react to an attack in progress. ASC alerts you in case of anomalies with user accounts such as failed or successful logon attempts, accounts that have their password changed or if there are accounts locked out because of their inappropriate behaviour.
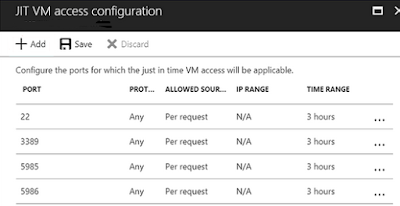
Another nice security feature is Just in time VM Access (JIT). If JIT VM Access is enabled, ASC allows you to create Network Security Group (NSG) rules and configure the access to VMs through these ports. Four port recommendations are already pre-configured, but not enabled, and you can add more later if you need to open a specific port.
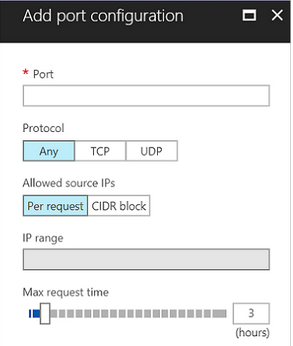
Adding a port is easy: give it a name, choose the applicable protocols, allowed source IP addresses (per request or per a block or range of addresses) and specify for how long the port will remain open or available to request access to.
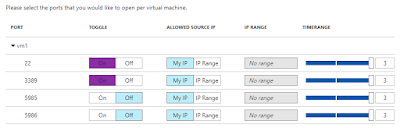
Later, when you want to request or give an access to a Virtual Machine (or Machines), select applicable VMs and click on Request Access in Just in time VM access blade. The Request access blade displays a list of configurable ports you can open after choosing allowed source IP addresses and a time range the ports will remain open.
This is just a part of the features and capabilities Azure Security Center offers. It can protect both VMs in Azure and on-premises VMs, supports application whitelisting, advanced threat detection capabilities and more.
There is more to securing the resources in Azure than doing it through ASC, but ASC is an invaluable asset that should be on every Azure administrator’s daily menu.
Microsoft Azure features and capabilities covered in Azure Security PowerClass cover additional topics that contribute to overall Azure security such as Azure Resource Manager, Log Analytics, Role-Based Access Control (RBAC), Encryption, Network Security Groups (NSG) and others.